In today’s digital age, the internet has become a vast space that we explore every day, from browsing our favorite social media platforms to checking out the latest news. But what if I told you that there’s a whole other side of the internet, one that remains largely hidden from the public eye? This is where the terms deep web and dark web come into play. While these terms are often used interchangeably, they refer to two very different parts of the internet.
Let’s dive in and uncover what makes the deep web and dark web unique, and why you should care about them.
What is The Deep Web?
Before we start diving into the darker parts of the internet, let’s first understand the deep web. To put it simply, the deep web refers to any part of the internet that isn’t indexed by search engines like Google, Bing, or Yahoo. This means that if you can’t find it using a simple search query, it’s probably part of the deep web. Now, don’t get the wrong impression. The deep web isn’t necessarily dangerous or illicit—it’s simply hidden.
Think of it as the layers beneath the surface of a webpage. This portion of the internet contains private data, personal information, and websites that aren’t meant for public viewing. A large chunk of the deep web consists of databases, academic resources, subscription-based services, and other private networks that require special access to view. The deep web is vast; it’s estimated that it makes up about 96% of the internet! Much of it is harmless and often used for privacy or security reasons. In fact, many businesses and organizations rely on it to keep their internal data safe and secure..
What is The Dark Web?
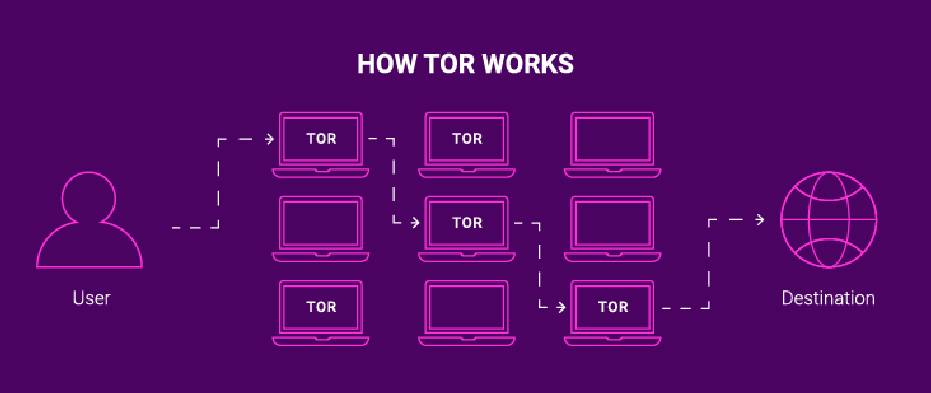
Now, let’s talk about the dark web. While the deep web is relatively benign, the dark web is the part of the internet that often raises eyebrows. It’s a small, intentionally concealed portion of the internet where illegal activities are often associated. The dark web is typically accessed via specific software like Tor (The Onion Router), which allows users to browse websites anonymously. Websites on the dark web often have a “.onion” domain extension instead of the usual “.com” or “.org.” These websites are not indexed by traditional search engines, making them harder to find.
The anonymity provided by Tor allows users to engage in activities without revealing their identity or location. The dark web is infamous for hosting marketplaces that deal in illicit goods, such as drugs, weapons, stolen data, and even human trafficking. In addition to this, it can also be home to forums where cybercriminals gather to discuss hacking techniques or coordinate illegal activities. While some individuals use the dark web as a tool for privacy, especially in countries with heavy internet censorship.
4 Main Differences Between the Deep Web and the Dark Web
Now that we have a basic understanding of both the deep web and dark web, let’s break down the key differences between them.
Accessibility
- Deep Web: It’s not hidden or illegal. Accessing the deep web is simple—just log into your email or access your bank account.
- Dark Web: Requires special software like Tor to access. It’s intentionally hidden and can be difficult to navigate.
Content
- Deep Web: Includes a variety of harmless content like academic databases, private company files, or subscription-based services.
- Dark Web: Contains both legitimate and illegal content. While some use it for anonymity and privacy, others exploit it for illegal activities.
Legality
- Deep Web: Entirely legal. The deep web is often used for privacy and security purposes.
- Dark Web: While accessing it isn’t illegal, many of the activities on the dark web are. Buying illicit goods or engaging in illegal activities can lead to serious consequences.
Size
- Deep Web: Enormous, making up the vast majority of the internet.
- Dark Web: Much smaller in comparison, it’s just a small fraction of the deep web.
Why Dark Web and Deep Web Matter?
With all this information, you may be wondering why the difference between the deep web and dark web matters to you. The truth is, in our digital world, understanding these hidden parts of the internet is crucial for maintaining privacy and safety. While the deep web is mostly harmless and can be essential for your personal online security, the dark web poses risks that you should be aware of, especially when it comes to online crime.
Being informed allows you to protect your personal information, avoid potential threats, and understand the broader scope of the internet beyond what we see on the surface. While the deep web and dark web may seem mysterious, knowing what lies beneath the surface helps you navigate the internet with a little more awareness. So, the next time someone mentions the deep web or dark web, you’ll be able to differentiate between the two and understand what’s really going on behind the scenes of the internet!